|
Counterintelligence
Counterintelligence is largely the practice of understanding OPSEC or Operations Security.
OPSEC is a military term that asks:
What can an adversary learn about our
organization by observing normal
day-to-day operations?
Operations Security defines your level of organizational privacy, and protects your trade secrets from unintentional leaks.
Everyday, uneducated employees, vendors, and contractors, leak vital organizational secrets by simply doing their jobs.
How are trade secrets leaked online?
Trade secrets are leaked by simply observing what you, and your employees, contractors, and vendors publish online.
HR & Job Postings
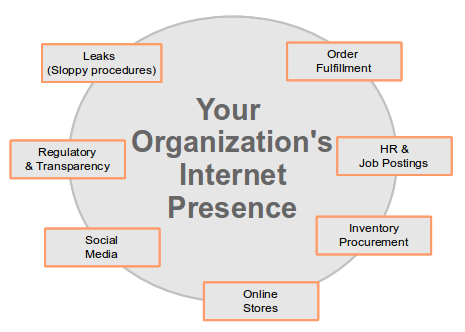 Many organizations leak strategic information in their job postings. This is
especially true when an organization is hiring in new skills in new locations.
HR Managers are seldom trained to post meaningful job postings in an era when their
job openings are periodically harvested by automated agents that are looking for
outliers in normal hiring activity.
Order Fulfillment
The way you fulfill orders can reveal a lot about your business. I've personally
been able to glean enough financial information about business from making periodic
orders to essentially be able to do their books.
Procuring Inventory
The way you buy inventory or other supplies from vendors can reveal how healthy your
business is, and how well diversified your sources are.
Online Stores
If not carefully planned and executed, your online store can leak your
pricing and brand strategies. It can also say a lot about your suppliers, customers,
and responsiveness to market changes.
Social Media
Your organization's use social media can leak information. And, the problems are multiplied by
the social media accounts of your employees, contractors, and vendors.
Often, social media can be used to determine, advanced word of new projects, employee rosters, and even customer lists.
Regulatory and Transparency
Many leaks are caused by rules and regulations intended for transparency. Without proper policy,
organization's leak strategic plans through financial, DNS, court, and intellectual property filings.
Leaks due to sloppy procedures
There is a long history of leaks that are caused by shear laziness, often leading to embarrassing situations.
Policies can be employed to limit these leaks.
Many organizations leak strategic information in their job postings. This is
especially true when an organization is hiring in new skills in new locations.
HR Managers are seldom trained to post meaningful job postings in an era when their
job openings are periodically harvested by automated agents that are looking for
outliers in normal hiring activity.
Order Fulfillment
The way you fulfill orders can reveal a lot about your business. I've personally
been able to glean enough financial information about business from making periodic
orders to essentially be able to do their books.
Procuring Inventory
The way you buy inventory or other supplies from vendors can reveal how healthy your
business is, and how well diversified your sources are.
Online Stores
If not carefully planned and executed, your online store can leak your
pricing and brand strategies. It can also say a lot about your suppliers, customers,
and responsiveness to market changes.
Social Media
Your organization's use social media can leak information. And, the problems are multiplied by
the social media accounts of your employees, contractors, and vendors.
Often, social media can be used to determine, advanced word of new projects, employee rosters, and even customer lists.
Regulatory and Transparency
Many leaks are caused by rules and regulations intended for transparency. Without proper policy,
organization's leak strategic plans through financial, DNS, court, and intellectual property filings.
Leaks due to sloppy procedures
There is a long history of leaks that are caused by shear laziness, often leading to embarrassing situations.
Policies can be employed to limit these leaks.
We provide organizational privacy training to help protect your organization's secrets.
|



